
Author: Alexandre Palma
Ransomware is malware that employs encryption to ransom a victim’s information. A user or organization’s critical data is encrypted so that they cannot access files, databases, or applications. A ransom is then demanded to provide access. Ransomware is often designed to spread across a network and target database and file servers and can thus quickly paralyze an entire organization. It is a growing threat, generating billions of dollars in payments to cyber criminals and inflicting significant damage and expenses for businesses and governmental organizations.
Different types of Ransomware Attacks
- Crypto Ransomware – This type encrypts the files and data within a system, making the content inaccessible without a decryption key.
- Lockers – This malware completely locks you out of your system, and your files and applications are inaccessible. A lock screen displays the ransom demand, possibly with a countdown clock to increase urgency and drive victims to act.
- Scareware – It is fake software that claims to have detected a virus or other issue on your computer and directs you to pay to resolve the problem. Some types of scareware lock the computer, while others only flood the screen with pop-up alerts without damaging files.
How does a Ransomware attack work
Ransomware enters your network in various ways; the most popular is a download via a spam email attachment. The download then launches the ransomware program that attacks your system. Other forms of entry include social engineering, downloads of malicious software from the web that can be direct from a site or by clicking on “advertising,” and fake ads that unleash the ransomware. The malware can also spread through chat messages or removable USB drives.
Typically, the software gets introduced to your network by an executable file that may have been in a zip folder, embedded within Microsoft Office document’s macros, or disguised as a fax or other viable attachment. The download file then encrypts your data, adds an extension to your files, and makes them inaccessible. More sophisticated versions of the software are propagating themselves and can work without any human action. Known as “drive-by” attacks, this way of ransomware infects your system through vulnerabilities in various browser plugins.
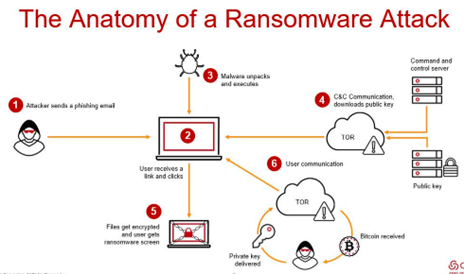
Figure 1- The anatomy of Ransomware (source: forbes.com)
How to prevent Ransomware Attack
- Make regular backups: Up-to-date backups are the most effective way of recovering from a ransomware attack (making regular backups of the most crucial files; ensuring the creation of offline backups that are kept separate in a different location; making multiple copies of files using other backup solutions and storage locations).
- Prevent malware from being delivered and spreading to devices: Reducing the likelihood of malicious content reaching your devices through a combination of some preventive actions (filtering to only allow file types you would expect to receive; blocking websites that are known to be naughty; actively inspecting content; use signatures to block known malicious code; etc.).
- Prevent malware from running on devices: The measures required to prevent malware from running on devices will vary depending on the device type, OS, and version, but in general, we need to pay attention and use device-level security features (centrally manage devices to only permit applications trusted by the enterprise to run on devices; consider whether enterprise antivirus or anti-malware products are necessary and keep it up to date; provide security education and awareness training to the employees; etc.).
- Prepare for an incident: Ransomware attacks, can be devastating for organizations because computer systems are no longer available, and in some cases, data may never be recovered. That’s a few steps that will help to recover quickly (Identify critical assets and determine the impact to these if they were affected by a malware attack; develop an internal and external communication strategy, this step is important to guarantee that the right information reaches the right stakeholders in a timely fashion; determine the response to the ransom demand and the threat of organization´s data being published; ensure that incident management playbooks and supporting resources such as checklists and contact details are available if the access to the computers is blocked; identify the legal obligations regarding the reporting of incidents to regulators; exercise your incident management plan, this helps clarify the roles and responsibilities of staff and third parties, and to prioritize system recovery).
(Source: National Cyber Security Center)
How to recover from a ransomware attack
- Recovery of data from backups, including verifying the integrity of those backups and understanding what data, if any, has been lost.
- Once compromised, EPPs and EDR, as well as MTD solutions, should be used as part of the remediation response to remove the threat and roll back any changes. As noted earlier, recovery goes beyond recovering the data; infected machines may be “locked” and may require physical access.
- During the preparation phase, it’s important to understand and plan for how this would be achieved.
- Validation of the integrity of a device before it is allowed back onto the network.
- Updating or removing compromised credentials; without this, the attacker will be able to gain entry again.
- Perform a thorough root cause analysis of how and what happened, including any data that has been exfiltrated (doxing). Doxing occurs when bad actors threaten to release stolen information. That is increasingly becoming a secondary method of extortion if a victim decides not to pay the ransom.
(Source: “How to prepare for ransomware attack” by Gartner)
3 Major ransomware attacks
Wanna Cry
In May 2017, Companies across the world were attacked by a fast-spreading piece of malware known as WannaCry. This ransomware infected 7000 computers in the first hour and 110000 distinct IP addresses in two days, making WannaCry one of the most notoriously destructive ransomware attacks of all time. Various entities in different industries lost control over their industrial processes, including car giants Renault and Honda.
WannaCry arrives via a phishing email and disseminates like a worm using covert channels and exploiting the Windows SMB vulnerability. The attackers first demanded $300 worth of bitcoins within 3 days and then later increased the ransom demand to $600 worth of bitcoins within 6 days.
In Portugal, the affected companies, including Portugal Telecom and EDP, decided to activate their security plans, restrict access, or disconnect their internal networks.
(Source: Swiss Cyber Institute)
TeslaCrypt
TeslaCrypt is popular ransomware that was discovered at the beginning of 2015. Since its first emergence, this ransomware underwent several version changes, with each version introducing new abilities and adding new evasion techniques. It started by utilizing social engineering to make a user click on a link in a phishing email and later added malicious attachments to these emails.
Regarding the malware distribution vector, TeslaCrypt was spread by the Angler and Nuclear browser exploit kits. Exploit kits are efficient tools for cybercriminals to distribute their malware. These kits exploit patched vulnerabilities in popular web technologies like Internet Explorer, Adobe Reader, Microsoft Silverlight, and Oracle Java.
This ransomware encrypts the user’s files and prompts a message asking the user $500 ransom in bitcoins to obtain the key to decrypt the files. Surprisingly, the creators of TeslaCrypt released the master decryption key to the public in 2016, shutting down their business model.
(Source: Swiss Cyber Institute)
Kaseya
On July 2, 2021, Kaseya announced its systems had been infiltrated. Kaseya provides IT solutions for other companies — an ideal target which, in a domino effect, ended up impacting approximately 1,500 organizations in multiple countries. REvil, a cybercriminal outfit, claimed responsibility for the attack and demanded ransoms ranging from a few thousand dollars to multiple millions, according to a Reuters report.
It’s unclear how many individual businesses paid up, but REvil demanded $70 million in bitcoin from Kaseya. Kaseya declined to pay, opting to cooperate with the FBI and the US Cybersecurity and Infrastructure Agency. On July 21, 2021, Kaseya obtained a universal decryptor key and distributed it to organizations impacted by the attack.
(Source: cnet.com)
Ransomware Statistics
- There were more than 304 million ransomware attacks worldwide last year. A new organization is attacked every 11-14 seconds.
- 73% of all ransomware attacks were successful in encrypting data.
- 55% of attacks hit businesses with 100 or fewer employees. 75% of attacks struck organizations with less than $50M in annual revenue.
- According to Microsoft, nearly 97% of all ransomware infections take less than 4 hours to successfully infiltrate their target. The fastest can take over systems in less than 45 minutes.
- Downtime due to ransomware increased by 200% over the past year.
- Downtime costs related to ransomware attacks are 2300% greater than the average ransom request.
- 27% of businesses that fell victim to ransomware made payments to hackers.
- The average ransom demand grew to more than $178,000 in 2020. However, the average ransom demand for an SMB is only $5,900.
- More than 95 new ransomware families have been discovered in the last 2 years.
- The global cost associated with ransomware recovery will exceed $20 billion in 2021.
(Source: Unitrends)
Conclusion
Nowadays it is highly important that all organizations are aware of and prepared for ransomware attacks. The adoption and the increasingly virtual and technological world open the door to new forms of robberies that can have serious consequences. Security is one of the fundamental pillars for the existence and development of any company and ensuring that companies are prepared for the increasing number of ransomware attacks is critical for CISOs to be actively managing.