Nowadays we are surrounded by technology, and a necessary implication or consequence of technology is cybercrimes. It all started with microcomputers in the 70s, and then cybercrimes appear, on that times the most popular at that time were “Brain Virus”, “Michaelangelo” and “Morris Worm”. When WWW emerged made web applications bloom. This blooming of course made the appearance of new cybercrimes techniques as we know them today, like, spyware, adware, spam, phishing, ransomware, DoS attack, etc.
The exponential growth and development of smartphones, cloud services, social media, and the Internet of Things (IoT) applications have motivated cybercriminals to innovate penetration tools and techniques and increase cyberattacks. Cybercriminals not only steal data but also disrupt operations and services. Improving cyber defense leads to higher levels of customer trust and increased revenue opportunities.
The annual cybersecurity spending worldwide has come increasing year over year, and that’s a tendency that will not slow by the data and the facts that we see. Technology is constant development and improvement and will never stop, so we should assume that cybercrimes will never end as well.
Global spending on cybersecurity products and services exceeded $1 trillion cumulatively over the five years from 2017 to 2021. This is a 12-15% year-over-year cybersecurity market growth from 2021 (Embroker, 2022).
The average number of security breaches grew by 11 percent from 130 in 2017 to 145 in 2018 per organization. An organization’s average cost of cybercrime increased from US$1.4 million to US$13.0 million (Accenture, 2019).
To measure cyber risk in management were developed different kinds of frameworks.
Cyber risk management needs to address both technical and human aspects holistically. Currently, there are many cybersecurity frameworks (e.g., NIST Cybersecurity Framework, ISO/IEC 27001, Control Objectives for Information and Related Technology (COBIT).
These frameworks provide activities, outcomes, and references that organizations can use to manage their cybersecurity risks.
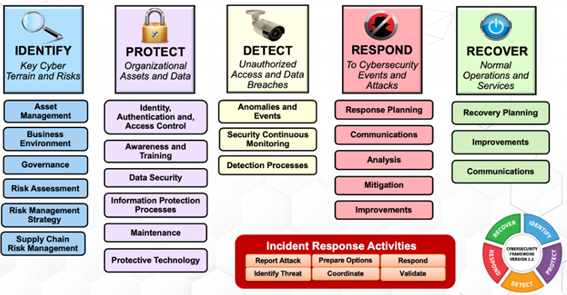
The NIST Framework consists of the Core, Profile, and Implementation Tiers. The Core provides activities, desired outcomes, and informative references that are common across different types of organizations. The Profile defines a customized set of activities, outcomes, and references based on an organization’s specific business environment and risk management priorities. The Implementation guides how to implement the NIST Framework within an organization.
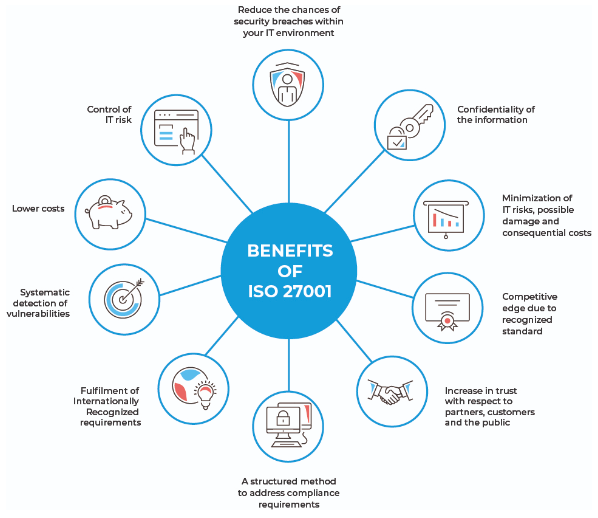
The ISO 27001 standard consists of fourteen sections divided into clauses. Section one provides an introduction, while section two defines the scope of the standard. section three contains the requirements for establishing, implementing, maintaining, and continually improving an information security management system. Sections four through thirteen contain the specific requirements for each of the ISO 27001 clauses. The final section, section fourteen, guides the implementation of the standard.
The CIS Critical Security Controls (CSC) is a set of twenty-three security controls that aim to provide defense-in-depth protection against the most common attacks. The controls are organized into five groups: Basic Controls, Foundational Controls, Organizational Controls, Operational Controls, and Information Protection Controls. The Basic Controls are the minimum controls that should be implemented to have an effective security program. The Foundational Controls build upon the Basic Controls and provide a more comprehensive set of controls. Organizational Controls address specific threats and vulnerabilities that are unique to an organization. The Operational Controls focus on the organization’s day-to-day operations, such as incident response and patch management. The Information Protection Controls provides a set of controls for protecting information from unauthorized access, use, disclosure, or destruction.

With the increased cybersecurity risks posed by cybercriminals and adversaries, it became imperative for organizations to increase their awareness of the change in the cybersecurity landscape and timely response to the change. The organization is responsible for identifying the need for cyber acquisition and the best technology to meet that need.