Cyber threats and attacks are increasing in volume, diversity, and pace as the digital world expands. There is an abundance of data around the globe, and someone is constantly trying to convert it into the virtual currency.

Now, everything from our personal cell phones to vital supply lines and infrastructure are being attacked by malware and ransomware. Attackers are also becoming more skilled as well, exploiting information about our personal and professional life to persuade us to reveal our data through phishing, smishing, or vishing.
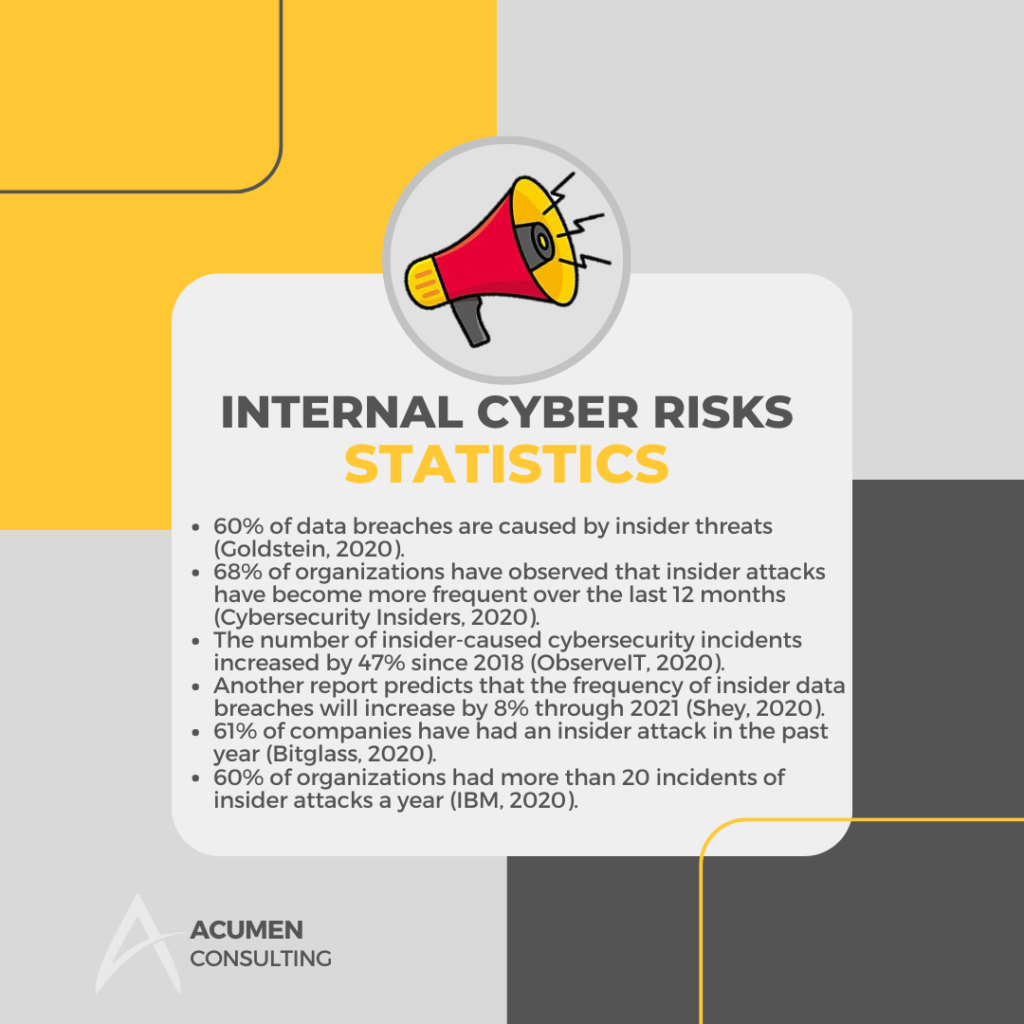
Nowadays, everyone is a target, so businesses must also be aware of the hazards that originate within their need to be aware of the hazards that originate within their own structures. More than 300 million people are working remotely now, and they can create, access, share, and store data anywhere.
1. Set up employee trust and privacy
This point comes first for a reason. Trust is the key to any functioning relationship in business and life. The best insider risk programs emphasize the balance between employee privacy and company security. It’s critical to come up with privacy controls and policies that maintain, and even boost, trust.
Putting up technologies to sift through employee activity for misbehavior is not just useless and unhelpful – it’s also wrong. It is an invasion of privacy that causes anxiety and deterioration in the relationship. Companies must be able to recognize insider threats and vulnerabilities, but they must do it correctly, operating publicly and within a tightly defined scope to demonstrate respect and trust to workers.
Setting up privacy settings that protect identities at work – even during investigations – shows that you care about them as well. Utilizing role-based access for insider risk management systems also ensures that the correct person is examining compliance alerts, preventing unnecessary suspicion from entering the business.
2. Cooperate across functions
While IT and security groups will lead the way, insider risk is a business problem that involves the entire company. At Microsoft, we learned this over time. What started as an initiative in our security organization evolved into a unified effort across the business groups, including legal, HR, and senior leadership.
This broad participation ensures broader buy-in and gives new viewpoints and resources, such as the legal department addressing upcoming rules and HR sponsoring training programs and surveys. An insider risk committee or ombudsperson might assist in starting the dialogue. One of their first tasks should be to develop a response strategy outlining how information is communicated, when and how much each group contributes, who makes which choices, and who is accountable.
It’s also critical to establish mutual goals with defined success metrics. You may improve the process by quantifying critical indicators including the number of instances raised, true positive and false positive flags, and actions performed as a result of the results. If you have a high number of false positives, you risk burdening your HR and legal teams with unnecessary and expensive investigations.
3. Remember that employees are the first and last line of defense
Encouraging staff to participate in data protection and compliance training can be difficult, but it is critical that they understand how to reduce security risks and why it is a priority. Training that stresses data stewardship indicates that the corporation trusts its workers to serve the business.
Teach employees how to appropriately manage the organization’s data and reinforce that message on a frequent basis to keep it fresh. It also helps to personalize it. Most individuals understand and act on how to secure their personal financial and healthcare data right away. Infusing a personal element into the training connects the dots on the necessity of data security for the organization.
Training people on the principle of “see something, say something” in a risk-free way is a critical capability for an insider program. By improving data security education and training, companies can empower employees as a first and last line of defense that is complemented by detection tools.
4. Adopt machine learning tools to do more with less
Gartner defines insider risk management as “the tools and capabilities to measure, detect, and contain undesirable behavior of trusted accounts within the organization.” And insider risk management tools have gotten much more precise and effective in recent years.
Older tools are prone to missing small clues that might indicate a bad actor attempting to cover their traces. They also frequently have too rigorous rules, which reduce productivity and promote workarounds. Insider risk management technologies with adaptive security capabilities that can identify dangerous actions and mitigate any possible damage while remaining out of the way and keeping user information private are emerging nowadays.
Although one conduct, such as printing secret information, may not suggest intent, a series of related acts, such as changing the file and then deleting it after printing, may indicate something more severe. Those technologies, which use machine learning, can separate the signal from the noise and identify minor activities, eliminating false positives that can bog down the company.
A successful insider risk program focuses on people, processes, and technologies.
Managing internal and external risks is vital to any organization’s security. Each comes with its own challenges, but what makes insider risk management especially tricky is the need to balance people, processes, and technologies. Powerful tools can help impede, detect, and respond to insider risks — but they won’t address the root causes. That’s where detailed onboarding, security training, team-building exercises, and work-life balance programs are useful. Building a healthy work environment helps reduce the risk of an employee intentionally engaging in dangerous behavior. But at the end of the day, striking the balance between people and technology matters most of all. Risk management must be proactive and continuous, and it takes trust, transparency, and collaboration to keep that engine running. This philosophy — people first, backed by powerful technology — is the only way to prevent incidents before they happen, detect them if they do, and respond to them quickly and effectively.